Understanding SCIM and Directory Sync
This article will walk you through everything you should know about SCIM and Directory Sync.

Head of Enterprise Integrations
This article will walk you through everything you should know about SCIM and Directory Sync.

Head of Enterprise Integrations
This article will walk you through everything you should know about SCIM and Directory Sync.
System for Cross-domain Identity Management (SCIM) is an open standard that allows for the automation of user provisioning (Directory Sync).
SCIM facilitates user identity data communication between Identity Providers (Okta, OneLogin, etc.) and Service Providers (Enterprise SaaS apps).
Many companies manually onboard and offboard users, which consumes many IT resources and time.
User lifecycle management (ULM) begins when employees start their job and continue until they leave the company. ULM is all about provisioning and de-provisioning users when they join an organization.
For IT departments, this means creating an account for the new employees in the cloud apps they need to use after starting their job. Also, IT departments must ensure that when those employees leave, they revoke access to those accounts.
Smaller organizations might address these procedures manually, but the process can become error-prone and time-consuming when done at scale. This is where the SCIM and Directory Sync come to the organization's rescue.
Directory sync helps organizations automate the provisioning and de-provisioning of their users.
As a result, it streamlines the user lifecycle management process by saving valuable organizational hours, creating a single truth source of the user identity data, and facilitating them to keep the data secure.
Directory sync allows programmatic access to the user identity data via a standard protocol (SCIM).
Directory sync implementation typically involves a client and a server. A client is an identity provider (IDP) with a directory of user identities. A service provider (SP) is an enterprise SaaS app that needs a subset of data from those identities.
When you make changes to the user identities, the changes are automatically synced to the SP according to the SCIM protocol. SP can now process this data according to the way they want.
Some common user identity changes include adding new users to the organization, updating existing users, removing users from the organization, adding users to groups, etc.
Technically, SCIM is a set of APIs that allows you to manipulate the users and group objects and expose these data as JSON through the REST endpoints.
Building Directory sync implementation yourself can be tedious and time-consuming for any engineering team.
Below are some questions the engineering team should answer before starting building Directory sync.
In short, building Directory sync yourself is not a good idea. It requires a lot of tedious engineering work and ongoing maintenance.
The best alternative is an open-source dedicated Directory Sync implementation provider like Ory Polis (formerly SAML Jackson) from Ory.
Ory can help enterprises to add Directory Sync to any SaaS app with just a few lines of code.
Enterprise SaaS apps can provide a Webhook endpoint Ory Polis, and Polis will notify the Webhook every time a change occurs in the user identity data within the IDP.
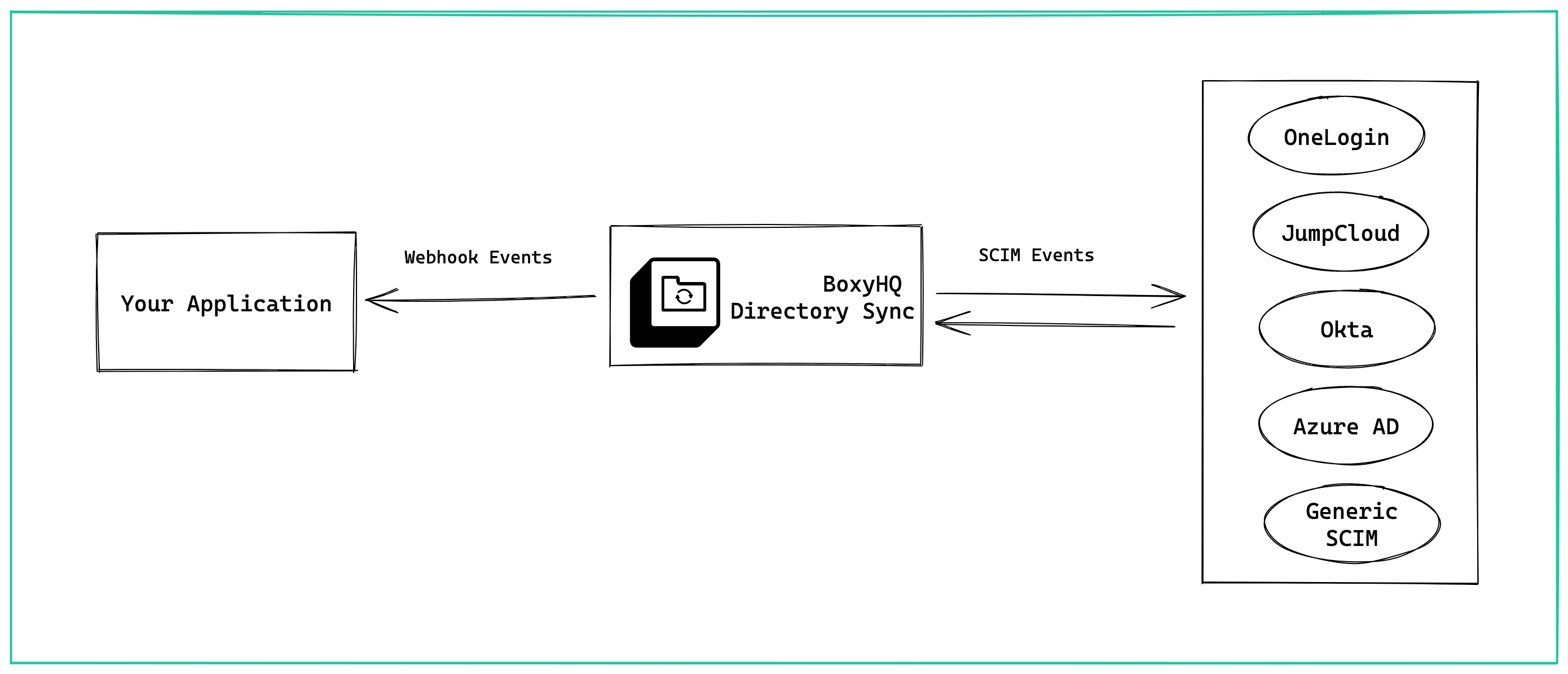
In short, Polis hides all the complexities involved with Directory Sync implementation and makes your integration easier.
Ory's Directory Sync implementation supports identity providers such as Okta, OneLogin, Azure AD, and JumpCloud. We're looking forward to adding more identity providers in future releases.
Here are a few critical aspects that make Ory's Directory Sync implementation stand out.
Directory Sync is a valuable investment for every organization seeking efficiency and security in their user lifecycle management system.
If you are interested in becoming enterprise-ready without the hassle, then let's chat! You can book a free consultation call and talk with our experts about how we can help. So let's start the journey together.